In our previous article in this Cybersecurity Series, we explored the latest developments in Malaysia’s cybersecurity framework and their impact on the regulated entities. Building on that, this article will explore the key duties and responsibilities under the Act
and its regulations.
Summary of the Key Duties and Responsibilities
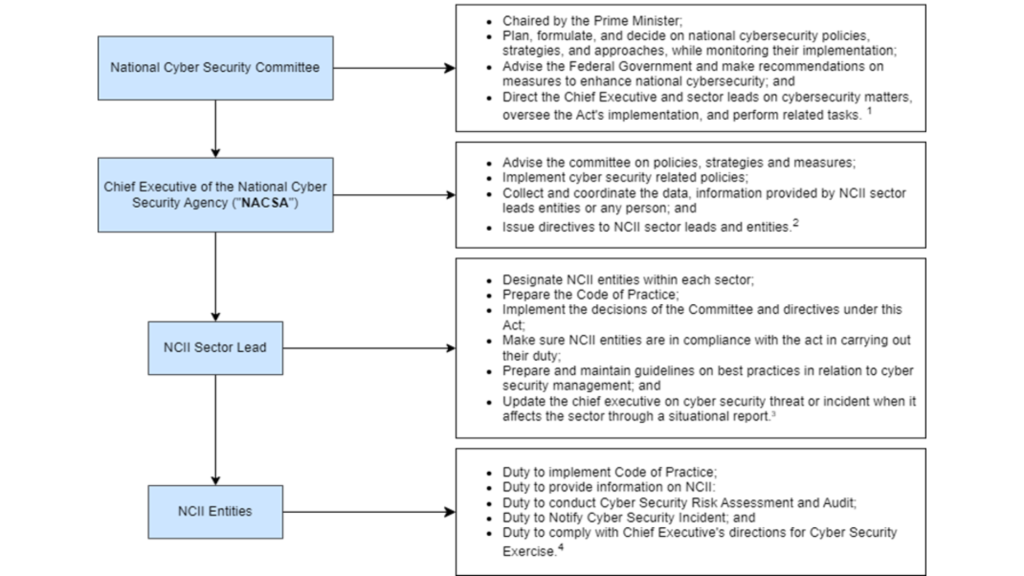
1. Duty to Provide Information on NCII:
Upon request by the NCII Sector Lead, the NCII Entity must provide relevant information about its NCII. If the NCII Entity acquires or has control over any new computer or system that is a NCII, it must notify the Sector Lead. Additionally, any material changes made to the design, configuration, security or operation of the NCII Entity must be report to the Sector Lead. [5]
2. Duty to Implement Code of Practice:
The NCII Entity must implement the measures, standards, and processes specified in the code of practice or adopt alternative methods to ensure the cybersecurity of its NCII. Although the relevant codes of practice are still under development, NCII Entities should consider adopting the standards under other international cybersecurity frameworks. [6]
3. Duty to Conduct Cyber Security Risk Assessment and Audit:
The NCII Entity shall conduct a cybersecurity risk assessment on its NCII at least once a year, and commission an audit by an auditor approved by the Chief Executive at least every two years. Following these assessments, the NCII Entity must submit the cybersecurity risk assessment report or audit report to the Chief Executive within 30 days of completion. [7]
4. Duty to Notify Cyber Security Incident:
If an NCII Entity becomes aware that a cyber security incident has or might have occurred in respect of its NCII, it shall report the incident immediately through the National Cyber Coordination and Command Centre System (NC4S). [8]
5. Duty to Comply with Chief Executive’s Directions for Cyber Security Exercise:
If the Chief Executive directs to conduct a cybersecurity exercise to assess the preparedness of any NCII Entity in handling cybersecurity threats or incidents, the NCII Entity is obligated to follow all instructions given by the Chief Executive. [9]
The NCII Entities are advised to take proactive steps now to align with the Act. Guidance can be obtained can be drawn from our neighbour Singapore, where a Code of Practice is already in place. Considering the similarity of the Act and the Singapore Cybersecurity Act 2018, it is reasonable to expect a comparable Code of Practice to be introduced in Malaysia.
Given the circumstances, the NCII entities should proactively budget for increased operational costs to comply with their duties and responsibilities under the Act. This will likely entail investing in advanced cybersecurity technologies and hiring qualified personnel to strengthen their cybersecurity teams. NCII entities can better position themselves to meet future obligations and mitigate cybersecurity risks effectively.
In our next article, we will closely examine the procedural steps outlined in the Act and its regulations for NCII entities to respond to cybersecurity attacks.
If you have any queries, please contact Associates Harvey Ng Yih Xiang (nyx@lh-ag.com) and Khew Gerjean (kgj@lh-ag.com), or their team Partner, G. Vijay Kumar (vkg@lh-ag.com).